CFW Ads Patch Record
GitHub - love98ooo/Clash_Ad_Patch: Remove auto-update and ads in Clash for Windows
What is it
CFW
-
CFW (Clash for Windows) is a Windows/macOS/Linux GUI based on Clash and Electron.
-
It is often used as a proxy tool in China.
Patch
-
CFW is a very efficient tool. However, it still has some functions that I do not want, like advertisements and the function of auto-updating.
-
I understand that those ads are income for the release author, so I will only remove the display of ads but still get ads images from the ads website. Hope that will help users and protect the author.
- But in all releases, the patch would directly block ads download and display. I will improve the patch in the next version.
-
In short, it is a patch to remove ads and the function of auto-updating.
How to use it
If you have not installed CFW
Releases · Fndroid/clash_for_windows_pkg · GitHub
-
According to your computer system choose the latest version, and then install it.
-
Follow the following steps.
If you have installed it
-
Quit your clash.
-
Download the latest 7z file from Releases · love98ooo/Clash_Ad_Patch · GitHub.
-
Extract it and then you will find
app.asar. -
Replace the
app.asarin {Your Clash Install Location}\resouces with the patch. -
Restart your Clash and you will find the ads have been removed.
If you are just finding a way to block the ads and have no interest in the technique, you can say “thanks” and close the website.
What I did when I made the patch
Searched for relative information
I found GitHub - ender-zhao/CFW-custom-made: Clash for Windows 机场专用版, 提供移除广告, 自定义广告, 移除更新版本 and the author also provided the tutorial to remove ads. However, the author had not updated since v0.19.0.
From his tutorial, I learned that the codes relative to ads and auto-update have been packaged in the \resources\app.asar.
About asar
We can find asar in Github: GitHub - electron/asar: Simple extensive tar-like archive format with indexing
Asar is a simple extensive archive format, it works like
tarthat concatenates all files together without compression, while having random access support.
We can follow the document in npmjs.
Here are two commands that we need to know:
-
asar pack|p <dir> <output>- Create asar archive
-
asar extract|e <archive> <dest>- Extract asar archive
Edited app.asar
Analysised app.asar
After extracting app.asar, we got a file including (only part of it):
│
├─dist
│ └─electron
│ │ renderer.js
│ │
│ ├─fonts
│ │
│ └─static
│
└─node_modules
Among those files, we only need to pay attention to renderer.js. (Renderer means “渲染器” in Chinese)
As expected, the file has been archived and there are only 8 lines. Luckily, it was written in Vue.js.
module.exports=function(e){function.../*!
/*!
* Vue.js v2.7.14
* (c) 2014-2022 Evan You
* Released under the MIT License.
*/
var n=Object.freeze({}),o=Array.is...
/*! @license DOMPurify 2.3.1 | (c) ...
Formated js codes
Reading all codes in one line is difficult for us, right? We need to format these codes. I recommend the following methods:
-
Use JetBrains IDE. It can format codes with Ctrl+Alt+L.
-
Use online tools like:
Of course, you can make your own wheels if you like.
Analysised renderer.js
When we are doing reverse engineering, we must focus on the content under quotes and meaningful function names.
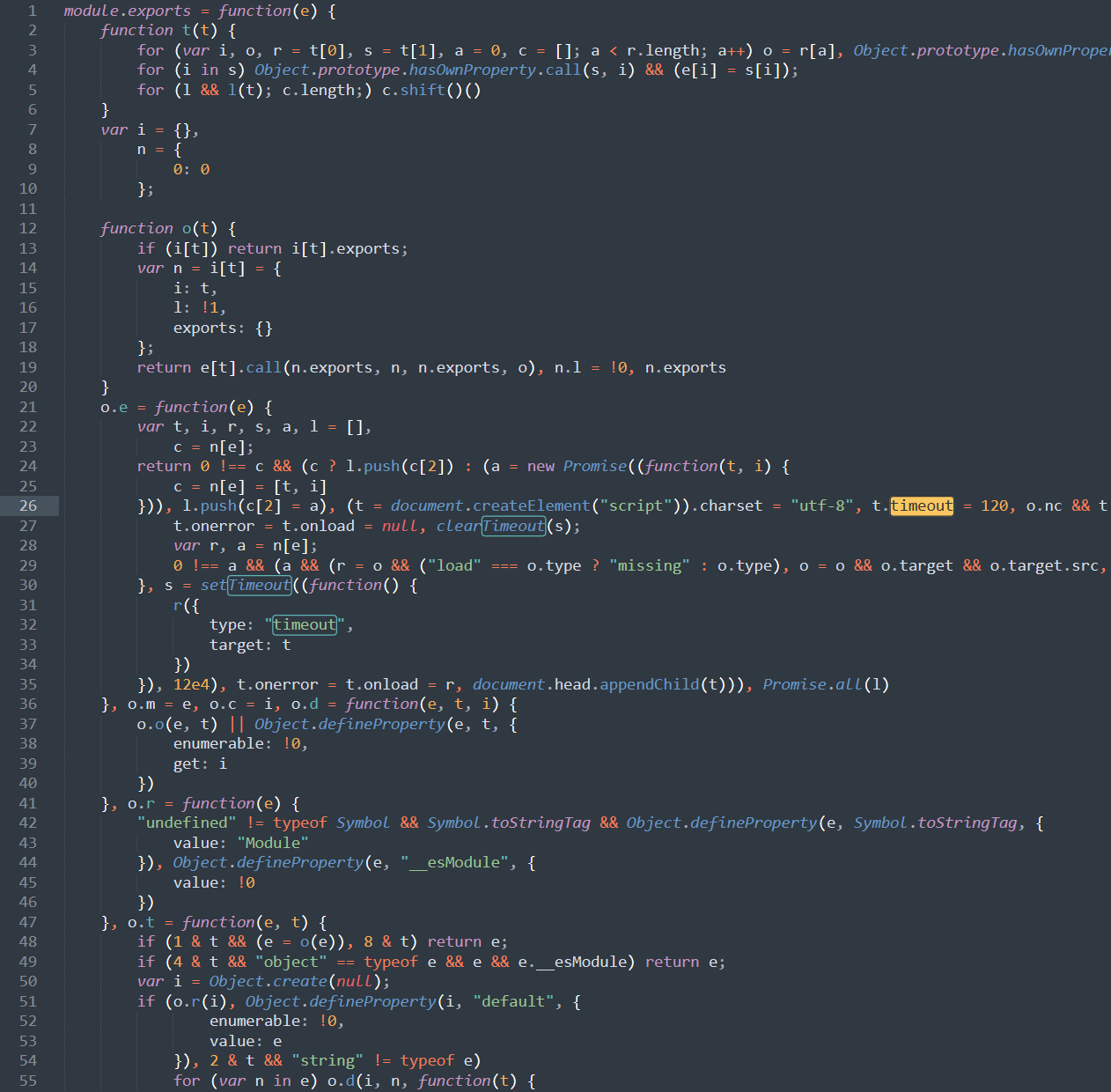
There are more than 100 thousand lines, and it is unrealistic to read all codes.
Searched “Feedback” and I found preDownloadAds in the context of one of the 49 results.
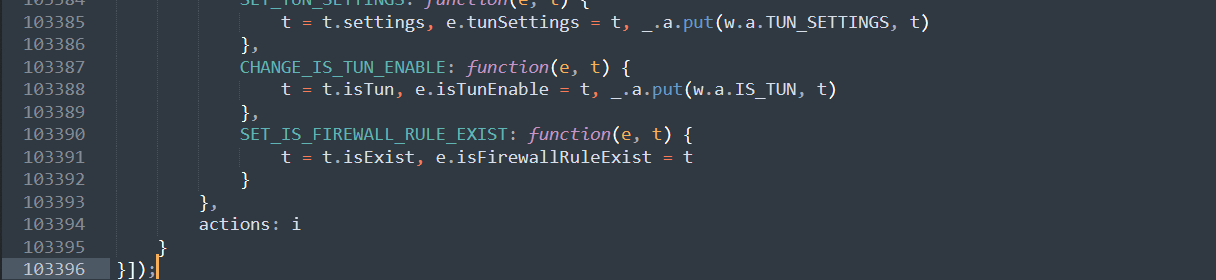
From the URL, I found the content in JSON format and the ad.
{
"feedback": [
{
"img": "https://down.suyunti.vip/ad.jpg",
"click": "https://suyunti.net/auth/register?code=3qcK"
},
{
"img": "https://tly33.com/asset/clash.gif",
"click": "https://tly.llc"
}
]
}

Followed the clue and I found the usage of the function.
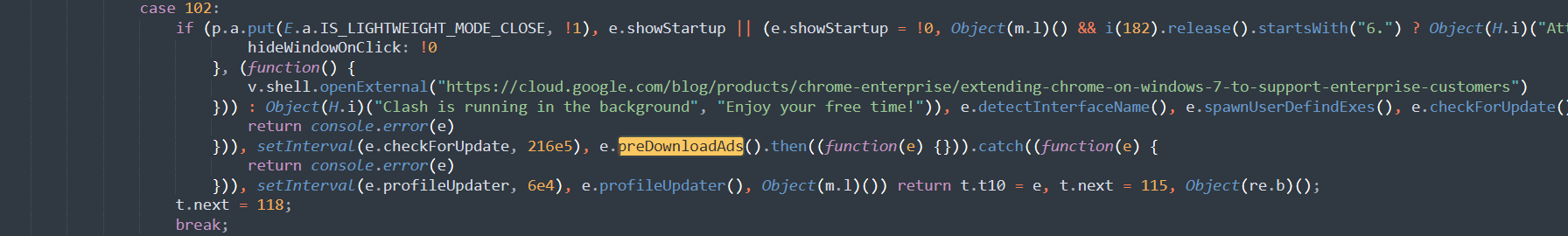
Since it was the only usage, if we could replace it with an empty function, the function preDownloadAds would not run. That meant no ads anymore.
It is one of the solutions.
By the way, I found the function checkForUpdate, and it was also very easy to locate its entrance with the same method.
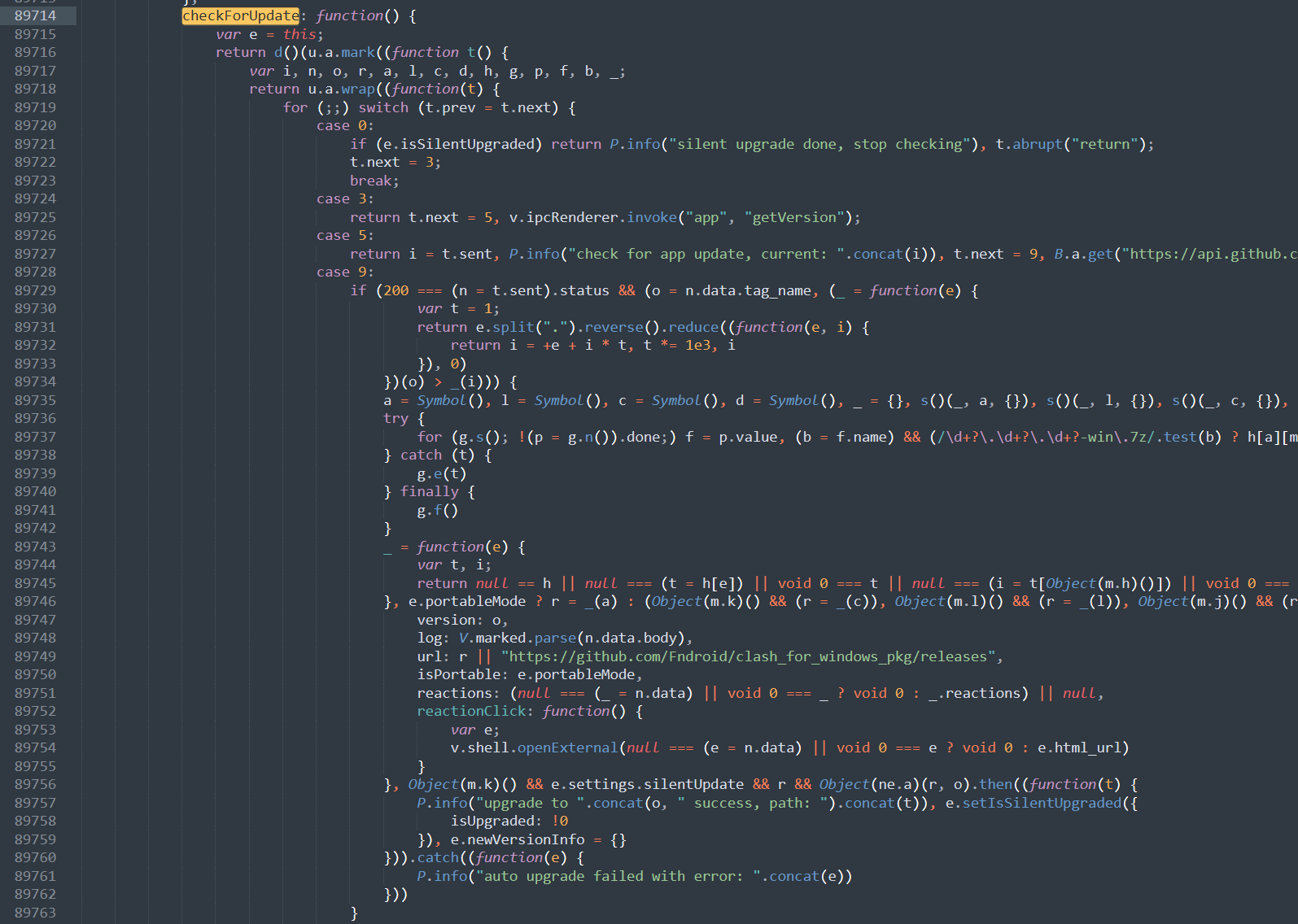
We could edit line 89715.(the line index is different when using different format tools)
var e = null
And then there is no way for CFW to update by itself.
Except for the front way to block ads, the title “Credit” was very close to “Advertisement”. As a result, we could also search Credits and find a series of objects with the same look.
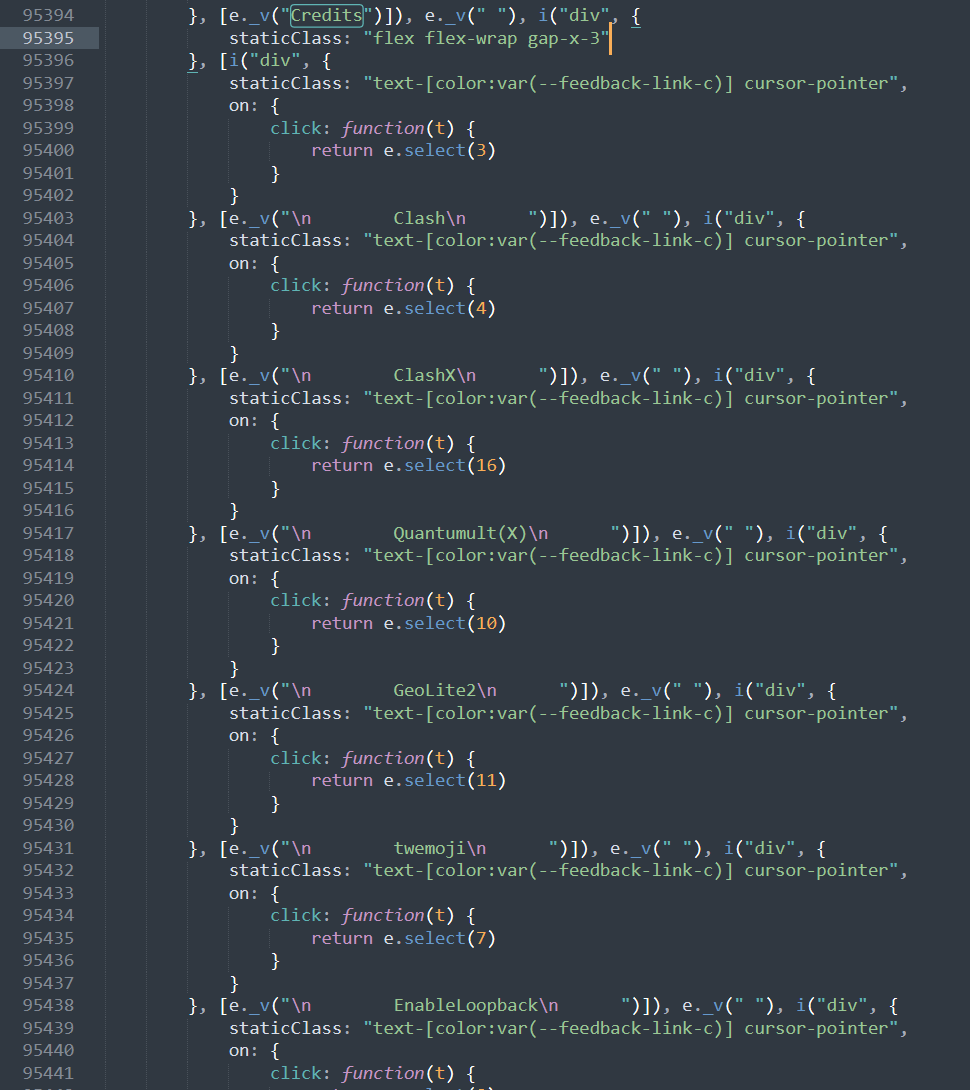
Pay attention to the content between \n and \n. Do you feel familiar? Right, it was the same as those links below Credits. Before I did the reverse engineering, I think the links were got from GitHub, but they were not.
Under Material Icons, I found Advertisement.

I guessed that it may relate to the display of ads. Let’s edit it.
[i("div", {
staticClass: "title"
}, [e._v("")]), e._v(" "), i("div", { //Remove Advertisement
staticClass: "ad-img-list"
}, e._l(null, (function(t, n) {
return i("div", {
key: null, //Replace n with null
staticClass: "ad-img"
}, [i("lazy-image-view", {
attrs: {
clickalbe: t.click,
src: null //Replace t.img with null
},
on: {
click: function(t) {
return e.adClick(n)
}
}
})], 1)
})), 0)]
Then, you would not see any advertisements, but maybe you would see two empty but clickable blocks. In the previous version, I remove every string containing “ad” and the function click return null as well.
As I said in front:
I understand that those ads are income for the release author, so I will only remove the display of ads but still get ads images from the ads website. Hope that will help users and protect the author.
I had no way to know how the author gets money from these ads, but I guessed that it had a relationship between the download times and the click times.
Repackaged app.asar
Finally, we come to the last process to make a patch. Save and close renderer.js and turn to path /app. Be careful, do not delete the original app.asar, you would not know whether your patch will run well. The more insurance method is to rename the app.asar first, and then in your terminal, input the package command asar p ./app ./app.asar.
The end
There are many ways to block the ads because programs are precise, and any little wrong could lead to a series of crashes. What programmers do is find the bugs and try their best to fix them. However, what I did is to make some man-made bugs so I think I need to say “sorry” to the CFW author for what I did.
If you readers have any questions about the article, please send me a private message.